
In today’s digital age, secure software development has become a paramount concern for developers, businesses, and end-users alike. As software increasingly underpins critical aspects of our daily lives—from financial transactions and healthcare systems to personal communications and entertainment—ensuring its secure software is more crucial than ever.
This Articles Contents
The Importance of Secure Software Development
While the primary goal of software development is to create functional and stable applications, security should never be an afterthought. Once a piece of software is deemed to be working and stable, focusing on its security is essential to protect it from vulnerabilities and threats that could compromise its integrity and functionality.
Common Issues with Software Stability and Bugs
Software development is inherently complex, and even the most meticulously crafted programs are susceptible to bugs and stability issues. These issues can arise from various sources, including coding errors, integration problems, and unforeseen interactions within the software environment. While achieving perfect stability is challenging, developers must strive to minimize these issues to create a robust foundation for security measures.
The Inevitability of Bugs
No software is entirely free of bugs. The inevitability of bugs underscores the importance of implementing comprehensive security practices. By acknowledging that vulnerabilities can exist, developers can adopt a proactive approach to identify and mitigate potential threats before they can be exploited.
In the following sections, we will delve deeper into the strategies and best practices for building secure web applications, understanding the OWASP Top 10 vulnerabilities, and exploring advanced security measures.
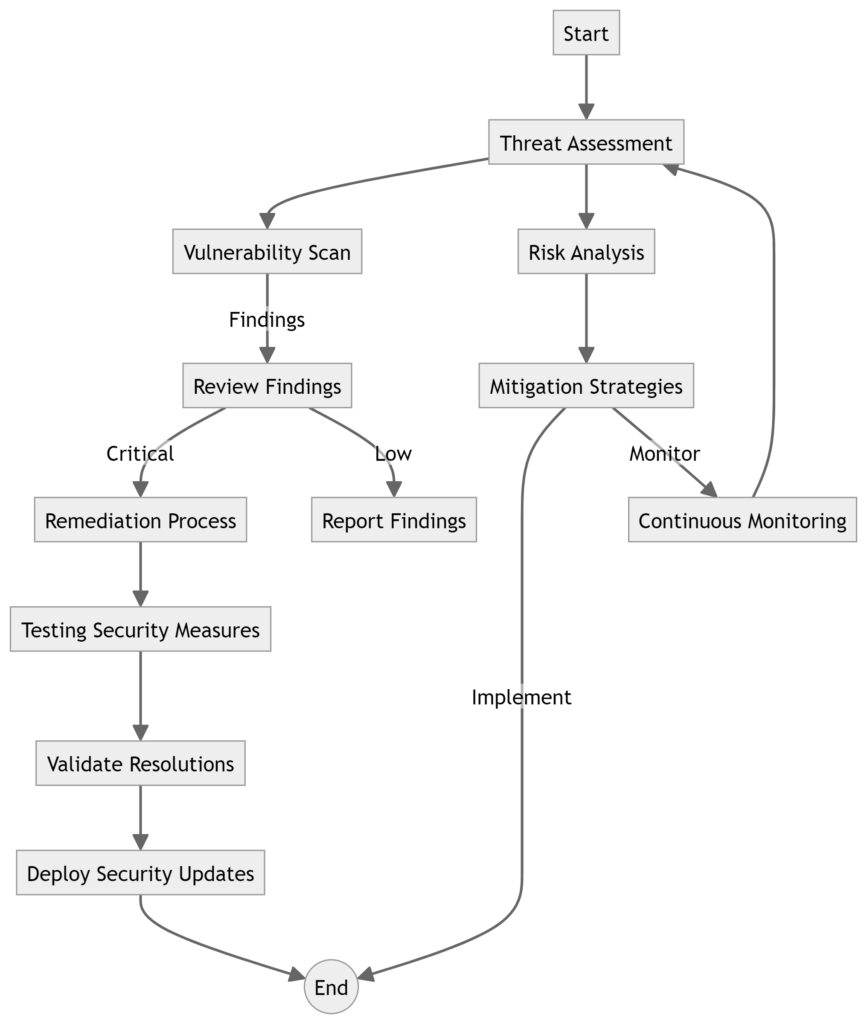
Building a Secure Web Application
In this step-by-step guide, we’ll walk you through the process of building a secure web application using Spring Security. From setting up a new project to implementing login and logout functionalities, and securing different resources, we’ve got you covered.
Step 1: Setting Up a New Project
- Create a New Spring Boot Project
- Use Spring Initializr (https://start.spring.io/) to generate a new Spring Boot project.
- Select the following dependencies: Spring Web, Spring Security, and Thymeleaf.
- Download the project and extract it to your desired location.
- Import the Project into Your IDE
- Open your preferred IDE (e.g., IntelliJ IDEA, Eclipse).
- Import the project as a Maven or Gradle project.
Step 2: Adding Necessary Dependencies
- Update
pom.xml(for Maven)
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>implementation 'org.springframework.boot:spring-boot-starter-security'
implementation 'org.springframework.boot:spring-boot-starter-thymeleaf'Step 3: Creating a Simple Web Application

- Create a Home Controller
- Create a new package named
com.example.demo.controller.Create a new Java class namedHomeControllerin this package.
- Create a new package named
package com.example.demo.controller;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.GetMapping;
@Controller
public class HomeController {
@GetMapping("/")
public String home() {
return "home";
}
}2. Create a Home View
<!DOCTYPE html>
<html xmlns:th="http://www.thymeleaf.org">
<head>
<title>Home</title>
</head>
<body>
<h1>Welcome to the Home Page!</h1>
</body>
</html>Step 4: Implementing Login and Logout Functionalities
- Create a Security Configuration Class
- Create a new package named
com.example.demo.config.Create a new Java class namedSecurityConfigin this package.
- Create a new package named
package com.example.demo.config;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
@Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/").permitAll()
.anyRequest().authenticated()
.and()
.formLogin()
.loginPage("/login")
.permitAll()
.and()
.logout()
.permitAll();
}
}- Create a Login Controller and View
- Create a new Java class named
LoginControllerin thecom.example.demo.controllerpackage.
- Create a new Java class named
package com.example.demo.controller;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.GetMapping;
@Controller
public class LoginController {
@GetMapping("/login")
public String login() {
return "login";
}
}- Create a new HTML file named
login.htmlin thetemplatesdirectory.
- Create a new HTML file named
<!DOCTYPE html>
<html xmlns:th="http://www.thymeleaf.org">
<head>
<title>Login</title>
</head>
<body>
<h1>Login</h1>
<form th:action="@{/login}" method="post">
<div>
<label>Username:</label>
<input type="text" name="username" />
</div>
<div>
<label>Password:</label>
<input type="password" name="password" />
</div>
<div>
<button type="submit">Login</button>
</div>
</form>
</body>
</html>Step 5: Securing Different Resources
- Update Security Configuration
- Modify the
SecurityConfigclass to secure different resources.
- Modify the
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/", "/home").permitAll()
.antMatchers("/admin/**").hasRole("ADMIN")
.anyRequest().authenticated()
.and()
.formLogin()
.loginPage("/login")
.permitAll()
.and()
.logout()
.permitAll();
}- Create Admin Controller and View
- Create a new Java class named
AdminControllerin thecom.example.demo.controllerpackage.
- Create a new Java class named
package com.example.demo.controller;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.GetMapping;
@Controller
public class AdminController {
@GetMapping("/admin")
public String admin() {
return "admin";
}
}- Create a new HTML file named
admin.htmlin thetemplatesdirectory.
- Create a new HTML file named
<!DOCTYPE html>
<html xmlns:th="http://www.thymeleaf.org">
<head>
<title>Admin</title>
</head>
<body>
<h1>Admin Page</h1>
</body>
</html>By following these steps, you will be able to create a simple yet secure web application using Spring Security. Remember that security is an ongoing process, and you should regularly check and update your application to protect against new threats.
Understanding OWASP Top 10
What is OWASP?
The Open Web Application Security Project, or OWASP, is an international non-profit organization dedicated to improving software security. It offers free resources and tools to assist enterprises improve their software security processes. One of OWASP’s most significant contributions is the OWASP Top 10, a frequently updated report that identifies the most serious security dangers to web applications.
Significance of the OWASP Top Ten
The OWASP Top 10 is a common awareness document for developers and online application security. It reflects a broad consensus on the most serious security threats to web applications. By concentrating on these top ten threats, businesses can drastically enhance their security posture and reduce the possibility of security breaches.
Overview of the OWASP Top 10 Security Risks
The latest OWASP Top 10 report lists the following security risks:
Broken Access Control
Description: Improperly imposed limitations on authenticated users allow them to access unauthorized functions or data.
Mitigation: Implement strong access control methods and frequently examine and test them.
Cryptographic Failures
Description: Insecure cryptographic storage and transfer of sensitive information.
Mitigation: Use robust encryption methods and keep cryptographic keys secret.
Injection
Description: Injection issues, including SQL, NoSQL, and command injection, arise when untrusted data is provided to an interpreter as part of a command or query.
Mitigation: To prevent injection attacks, use parameterized queries and input validation.
Insecure Design
Description: Flaws in the application’s design render it inherently vulnerable.
Mitigation: Incorporate security into the design phase by adhering to secure design principles and performing threat modeling.
Security Misconfiguration
Description: Insecure default settings, inadequate configurations, or ad hoc configurations.
Mitigation: Implement secure configurations for all components, which should be reviewed and updated regularly.
Vulnerable and Outdated Components
Description: Using components with known vulnerabilities or out-of-date software versions.
Mitigation: Regularly update and patch all components, and employ vulnerability identification tools.
Identification and Authentication Failures
Description: Weak authentication techniques enable attackers to compromise user credentials.
Mitigation: Implement multi-factor authentication and maintain password security.
Software and Data Integrity Failures
Description: Code and infrastructure that do not prevent integrity violations.
Mitigation: Utilize digital signatures, checksums, and secure updating mechanisms.
Security Logging and Monitoring Failures
Description: A lack of adequate logging and monitoring makes it harder to notice and respond to security incidents.
Mitigation: Implement thorough logging and monitoring solutions and conduct regular log reviews.
Server-Side Request Forgery (SSRF)
Description: SSRF issues occur when a web application is misled into sending requests to unwanted destinations.
Mitigation: Validate and sanitize all inputs, and employ network access controls to avoid unauthorized requests.
Practical Advice on Mitigating OWASP Top 10 Risks
- Conduct Regular Security Assessments: To detect and address vulnerabilities, conduct security assessments on a regular basis, which may include penetration testing and code reviews.
- Implement Secure Coding Practices: To reduce the possibility of security problems, adhere to secure coding rules and utilize security frameworks and libraries.
- Educate Developers: Provide constant security training to developers so that they are up to date on the latest security risks and best practices.
- Use Automated Security Tools: Use automated static and dynamic analysis techniques to detect and address security concerns early in the development lifecycle.
- Adopt a Security-First Mindset: Make security a priority throughout the software development lifecycle, from design to deployment and maintenance.
Understanding and resolving the OWASP Top 10 security concerns allows enterprises to greatly improve the security of their online applications and protect against typical attackers.
Advanced Security Measures
In this section, we will delve into advanced security measures that are critical for safeguarding web applications. These measures include cryptography, access control, and handling injection attacks. Each of these techniques is essential for creating a robust security framework. Let’s explore these topics in detail.
Cryptography
Cryptography is the art of safeguarding information by converting it into an unreadable format that can only be accessed by those with the appropriate decryption key. This ensures that unauthorized parties cannot interpret the intercepted data. Here are a few crucial practices:
- Use Strong Encryption Algorithms: Always utilize well-known and robust encryption methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman). Avoid using old algorithms such as DES (Data Encryption Standard).
- Encrypt Sensitive Data: Always utilize well-known and robust encryption methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman). Avoid using old algorithms such as DES (Data Encryption Standard).
- Key Management: Properly maintain encryption keys. To reduce the danger of key compromise, use secure key storage methods and rotate them on a regular basis.
Access Control
Access control systems ensure that only authorized users have access to specific resources within a web application. Implementing strong access control methods can help avoid illegal access and data breaches. Below are some best practices:
Role-Based Access Control (RBAC): Instead of assigning permissions to people, use roles. This streamlines management and guarantees that users only have access to what they require.
Least Privilege Principle: Allow people to have the least amount of access required to complete their responsibilities. This mitigates the potential consequences of a compromised account.
Multi-Factor Authentication (MFA): Implement multi-factor authentication (MFA) to add further protection. Users must submit two or more verification factors to get access.
Handling Injection Attacks
Injection attacks, such as SQL injection, pose a significant threat to web systems. These attacks occur when an attacker can transmit malicious code via input fields, which the application then executes. Here are some ways for reducing injection attacks:
- Input Validation: Always validate and sanitize user input. Whitelisting allows just accepted input values.
- Parameterized Queries: To prevent malicious SQL code injection, use parameterized queries or prepared statements.
- Regular Security Audits: Conduct regular security audits and code reviews to detect and resolve vulnerabilities before they are exploited.
By implementing these advanced security measures, you can significantly enhance the security posture of your web application. Always stay updated with the latest security trends and continuously improve your security practices. For more foundational security practices, refer to the Introduction to Software Security section.
Conclusion and Best Practices
Implementing these advanced security techniques can greatly improve the security posture of your web application. Keep up with the newest security developments and always enhance your security processes. Refer to the “Introduction to Software Security” section for more information on basic security techniques.
Key Takeaways
- Focus on Functionality and Stability First: Before you begin implementing security measures, make sure your application is functional and stable. A non-functional application cannot be properly secured.
- Importance of Security: Security is essential. Without adequate security measures, your application is subject to assaults that may jeopardize data integrity, user privacy, and overall trust in your product.
- Role-Based Access Control: Implement role-based access control to ensure that users can only conduct actions appropriate for their role. This is critical in applications such as e-commerce platforms, where various users have varying degrees of access.
- Spring Security: Using frameworks like Spring Security may greatly ease the process of securing your web application. It includes built-in authentication and authorization features, making it easier to establish security from the start.
- OWASP Top 10: Familiarize yourself with the OWASP Top 10 security threats and make sure your application is secure against these frequent vulnerabilities. This includes safeguards against injection attacks, compromised authentication, the disclosure of sensitive data, and other threats.
Best Practices
- Regular Updates: To avoid known vulnerabilities, keep your frameworks, libraries, and dependencies up to date.
- Penetration Testing: Penetration testing should be performed on a regular basis to discover and resolve security flaws before they are exploited by attackers.
- Secure Coding Practices: To avoid typical security issues, implement secure coding standards such as input validation, output encoding, and effective error handling.
- Use Strong Authentication: Implement strong authentication systems, such as multi-factor authentication, to improve cybersecurity. Avoid using the default or weak passwords.
- Encrypt Sensitive Data: Encrypt sensitive data both in transit and at rest to prevent unauthorized access.
- Monitor and Audit: Monitor your application for unusual activity on a continuous basis, and conduct regular security audits to assure compliance.
- Educate Your Team: Ensure that all team members are aware of best practices for security and understand their role in keeping the application secure.
By adhering to these best practices and constantly enhancing your security measures, you can create a strong and secure web application that can resist the ever-changing world of cyber attacks. Remember that security is a continuous process, and remaining alert is critical to protecting your application and its users.